Lost Your Phone? Do not Get Hooked: A Guide to Avoiding Phishing Pitfalls.

In an era where our lives are one with our smartphones, the high rate of increase of theft presents a twofold menace. From the daring exploits of home invaders to the skillful fingers of pickpockets in crowded spaces, the methods employed to snatch these technological lifelines vary widely. Yet, these acts extend beyond the physical world. Their criminal intentions extend to extracting sensitive information stored within, potentially leading to identity theft, financial loss, and even unauthorized access to personal data.
This blog post ventures into the complex landscape of smartphone security, unveiling a dual threat that goes beyond the tangible and the virtual. From daring thefts that result in physical possession to the covert tactics of phishing via SMS known as Smishing, a range of techniques used by the modern-day criminal to exploit both the device and the unsuspecting user.
Understanding the Threat: Decoding the Tactics of Modern Smartphone Thieves.
In the twisted dance between technology and criminal ingenuity, smartphone theft has grown beyond mere physical possession. Understanding the threat requires us to uncover the multifaceted strategies employed by modern-day thieves—a narrative that spans both tangible and virtual realms.
The Physical Onslaught:
Home break-ins, car break-ins, and pickpocketing are age-old techniques, yet their resurgence in the digital age adds an extra layer of complexity. Thieves don’t just target valuables; they aim for smartphones serving as gateways to our personal and digital worlds. Pickpockets armed with quick fingers seek to vanish with our devices but to exploit them for gains.
The Defensive Reflex and Cybernetic Intrusion:
With every modern smartphone user, the first line of defense is swift and decisive—activating the stolen phone lock mechanism provided by the device manufacturer. For instance, Apple users turn to the robust Find My iPhone feature. However, this defensive reflex, though crucial, sets the stage for a disturbing twist. Thieves, equipped with the stolen phone and the victim’s locked screen details, embark on a phishing quest, leveraging SMS messages that mimic official communication. The victims, driven by the urgency to locate their device, hand over login credentials without being aware, providing thieves with the golden key to unlocking stolen devices.
As these dual threats converge, the stakes heighten. The stolen smartphone transforms into a potential weapon, compromising personal information and paving the way for identity theft and unauthorized access.
Common Phishing Tactics: Navigating the Web of Deceit.
Having understood the multifaceted nature of smartphone theft, we now look at the specific tactics employed by modern-day thieves, particularly in the cyber-world of intrusion and phishing attempts. The stolen phone lock mechanism, activated by the victim, serves as a crucial barrier, but innovative criminals exploit the urgency and anxiety that often follow such thefts.
The Trojan-SMS:
The moment the victim activates the stolen phone lock mechanism, the race against time begins. The Thieves, aware of this urgency, start a blast of phishing attempts through SMS messages to the number displayed on the lock screen. These messages often masquerade as urgent notifications from the device manufacturer or service provider, creating an atmosphere of crisis that prompts users to act swiftly.
The Mimicry Game:
Crafty criminals employ sophisticated mimicry techniques, making their SMS messages virtually identical to official communications. Victims, eager to regain control of their locked phones, may not scrutinize these messages closely, falling victim to the deceptive skills of the Phisher.
The Click-and-Capture Trap:
Embedded within these deceptive messages are links that, once clicked, redirect users to cloned login sites. These sites, with great attention to detail, designed to replicate the authentic login pages of device manufacturers or service providers, deceive users into entering their credentials. Without knowing, they have just handed over the virtual keys to their digital kingdom.
Recognizing Phishing Attempts: A User’s Guide to Digital Vigilance.
As we navigate the web of deceit spun by cybercriminals, the ability to spot phishing attempts becomes paramount. The urgency and mimicry inherent in Smishing attacks can catch even the most cautious users. In this section, we’ll explore key strategies to empower you in identifying and preventing these deceptive operations.
- Assess the Tone and Urgency:
Phishing messages thrive on creating a sense of urgency. Beware of SMS messages that demand immediate action, threaten consequences, or convey a heightened sense of emergency. Authentic communications, while prompt, typically maintain a professional and informative tone.
- Check for Red Flags:
Carefully examine the content of the SMS message for red flags, such as grammatical errors, spelling mistakes, or unusual formatting. Cybercriminals often overlook these details in their rush to deploy phishing attempts, providing discerning users with valuable clues.
- Verify Website Authenticity:
If a message contains a link to a login page, resist the urge to click impulsively. Instead, manually navigate to the official website or app of the device manufacturer or service provider. Confirm the legitimacy of the message and the associated action through trusted sources.
Examples
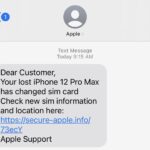 |
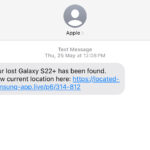 |
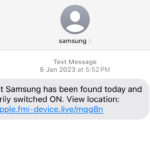 |
By incorporating these strategies into your digital habits, you can strengthen your defenses against phishing attempts via SMS. By sharpening the skill of recognizing these deceitful tactics, users can safeguard their personal information and confidently navigate the digital space.
What to Do If You Suspect a Phishing Attempt: A Step-by-Step Guide.
Despite our best efforts, there may be instances where the line between a legitimate message and a phishing attempt blurs. In such cases, it’s essential to know how to respond effectively. Here’s a step-by-step guide to follow if you suspect a phishing attempt:
- Pause and Verify:
Take a moment to pause and assess the message. Resist the urge to click on any links or provide information impulsively. Phishers rely on urgency; slowing down can be your first line of defense.
- Cross-Verify Through Official Channels:
Manually go to the official website or app of the alleged sender. Avoid using any links provided in the suspicious message. Confirm the legitimacy of the communication directly from trusted sources.
- Report the Suspicious Message:
Most smartphone manufacturers and service providers have mechanisms for reporting phishing attempts. Forward the suspicious message to the official reporting channels. This action helps these entities take action against potential threats. The CSA has a form on its official website for reporting cybersecurity-related issues, or you can use any of the below channels.
Email:report@csa.gov.gh
Call:292
SMS: 292
WhatsApp: 0501603111
Mobile App: CSA Ghana
- Update Passwords Immediately:
If you have mistakenly provided login credentials, change your passwords immediately. The update is crucial to prevent unauthorized access to your accounts and mitigate potential risks across your cyber world.
- Enable Additional Security Measures:
Consider implementing additional security measures, such as changing your account settings or enabling extra authentication methods. By doing so can add an extra layer of protection against unauthorized access.
- Educate Others:
Share your experience with friends, family, and colleagues. Educating others about potential threats fosters a collective sense of digital awareness and safety. You can also share your experience in the comment section.
By following these steps, you protect yourself and contribute to the broader effort of combating cyber threats. Remember, a vigilant and informed community is the bedrock of a secure digital environment. Stay cautious, stay secured. My ultimate piece of advice: when activating your lost phone mechanism, use the contact of someone who is a neutral party.

